Social Engineering Simulation by the Ministry of Education
In accordance with Article 8 of the “Information and Communication Security Incident Reporting and Response Guidelines” and relevant provisions of the “Taiwan Academic Network Management Regulations,” the Ministry of Education will officially launch a Social Engineering Simulation on Malicious Email Prevention, effective immediately. All faculty and staff are reminded not to open suspicious emails, particularly those sent from non-governmental sources, and are advised to prepare accordingly.
Target Participants: All university faculty and staff
Simulation Schedule: Two simulation exercises will be conducted during the designated period
Purpose of the Simulation
To enhance the awareness of faculty and staff within educational institutions and reduce the risks associated with social engineering attacks, this simulation aims to emulate various phishing techniques commonly used by malicious actors. By assessing the click-through rate of deceptive emails among faculty and staff, the exercise seeks to reinforce cybersecurity awareness and promote vigilance against social engineering and related threats.
Simulation Methodology
- The simulation team designated by the Ministry of Education will send malicious emails to school personnel under various disguises, such as official government notices, personal messages, corporate communications, or weekly bulletins.
- Email subjects will cover a wide range of themes, including politics, government affairs, health and wellness, shopping, finance, gaming, gossip, medicine, adult content, and travel. Each email may contain embedded hyperlinks or file attachments.
- Any faculty or staff member who opens such emails or clicks on the links or attachments will be considered to have failed the simulation.
Important Reminder
- Failure to pass the social engineering simulation may significantly impact the Ministry of Education’s evaluation of our institution. Depending on the circumstances, results may be reported during administrative meetings.
- To assist with email security, our office has provided key configuration guidelines. Please ensure that all recommended settings are properly applied. For assistance, contact the Web Media Section at extension 2325.
- Official university email accounts must not be used to receive personal emails. Faculty and staff are kindly requested to use their personal email accounts for private correspondence and to implement appropriate email security settings.
- During the simulation period, do not open any suspicious emails—especially those from unknown senders, with sensational subject lines, or containing links designed to entice clicks. Please delete such emails immediately. Forwarding suspicious emails is considered equivalent to opening them; therefore, do not forward these messages to your personal account or to others.
The subject lines used in past simulation emails from the Ministry of Education have been highly diverse, covering themes such as health, technology, beauty, finance, novelty, and travel. These subject lines are deliberately crafted to entice recipients into opening the emails and falling for the bait.
Please remain extremely vigilant and exercise caution when handling suspicious emails!
Summary of Past Email-
Based Social Engineering Simulation Results by the Ministry of Education
As shown in the table of past annual simulation results, the outcomes have consistently fallen short of the Ministry of Education’s expected benchmarks. To strengthen cybersecurity awareness among faculty and staff, the university will continue to promote information security concepts. Personnel who fail to pass the Ministry’s simulation will be identified as priority participants for future cybersecurity awareness campaigns and training programs.
Similar simulations may be conducted irregularly each year by the Ministry of Education or the Executive Yuan. Therefore, the university has compiled the data and results from this exercise, along with key precautions, for reference by all users.
Batch | Number of Test Participants | Number of Emails Opened | Email Open Rate | Number of Link Clicks | Click-Through Rate |
|---|---|---|---|---|---|
Batch 2, Year 2024 | 100 | 20 | 20% | 8 | 8% |
Batch 1, Year 2024 | 100 | 23 | 23% | 6 | 6% |
Batch 2, Year 2023 | 100 | 14 | 14% | 1 | 1% |
Batch 1, Year 2023 | 100 | 23 | 23% | 3 | 3% |
Batch 2, Year 2022 | 100 | 19 | 19% | 8 | 8% |
Batch 1, Year 2022 | 100 | 11 | 11% | 22 | 22% |
Ministry of Education Compliance Standards
- The email open rate for malicious messages must be below 10%.
- The click rate for malicious links or attachments must be below 6%.
本校受測結果
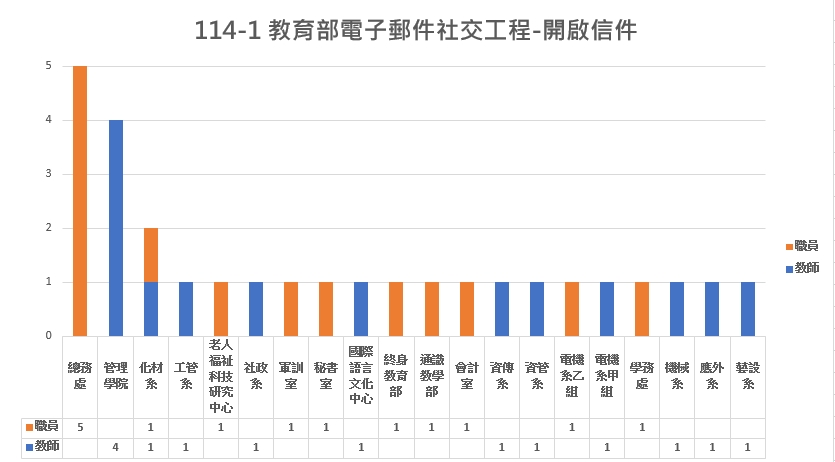
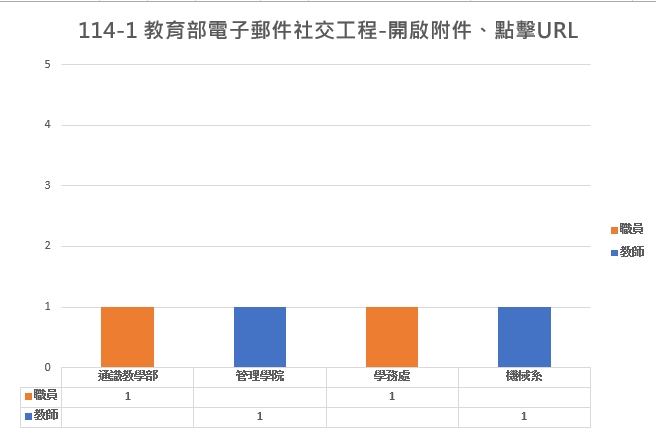
113-1 Social Engineering Test Email Subjects
- Impersonation Category Convenience Store Voucher – NT$1,000 Serial Code Notification (Please claim within 1 hour)
- Technology Category Attention iPhone Users! New Virus “Steals Banking Data” – Victims Concentrated in Asia
- Travel Category Beigang Sugar Factory Railway Landscape Cultural Space Completed – A New Look for the Historic Site
- Current Affairs Category Telecom Anti-Fraud Voice Service Launched! Think Twice Before Answering If You Hear These “14 Words”
- Beauty & Wellness Category Taking Supplements for Better Skin? Nutritionist Explains 5 Key Ingredients to Avoid Wasting Money
113-1 Social Engineering Test Email Subjects
- Impersonation Category Convenience Store Voucher – NT$1,000 Serial Code Notification (Please claim within 1 hour)
- Technology Category Attention iPhone Users! New Virus “Steals Banking Data” – Victims Concentrated in Asia
- Travel Category Beigang Sugar Factory Railway Landscape Cultural Space Completed – A New Look for the Historic Site
- Current Affairs Category Telecom Anti-Fraud Voice Service Launched! Think Twice Before Answering If You Hear These “14 Words”
- Beauty & Wellness Category Taking Supplements for Better Skin? Nutritionist Explains 5 Key Ingredients to Avoid Wasting Money
113-2 Social Engineering Test Email Subjects
- Government Affairs Category Executive Yuan Confirms: Salary Increase for Military, Civil Servants, and Teachers Next Year
- Adult Content Category Shocking Announcement! 40-Year-Old Chen Yi Teases “Pre-Battle Reveal” Before Entering the Industry
- Travel Category Travel Subsidy Boosted – Group Tours and Independent Travel Eligible! Claim NT$1,000 if Qualified
- Travel Category [Taitung Hot Air Balloon Festival Guide] Sanrio Collaboration and Light Sculpture Concert Highlights
- Impersonation Category “Fully Transparent Text” Trick Makes Your iPhone Lock Screen Look Premium – Protect Your Privacy
113-2 Social Engineering Test Email Subjects
- Government Affairs Category Executive Yuan Confirms: Salary Increase for Military, Civil Servants, and Teachers Next Year
- Adult Content Category Shocking Announcement! 40-Year-Old Chen Yi Teases “Pre-Battle Reveal” Before Entering the Industry
- Travel Category Travel Subsidy Boosted – Group Tours and Independent Travel Eligible! Claim NT$1,000 if Qualified
- Travel Category [Taitung Hot Air Balloon Festival Guide] Sanrio Collaboration and Light Sculpture Concert Highlights
- Impersonation Category “Fully Transparent Text” Trick Makes Your iPhone Lock Screen Look Premium – Protect Your Privacy
Principles of Social Engineering
Social engineering is a form of deception that exploits human vulnerabilities to achieve personal gain. One of the most commonly used tools is email, through which attackers lure recipients into opening messages or clicking on links. These emails often contain malicious software or embedded links. Once clicked or opened, the attacker may gain control or access to the user’s system.
Social engineering techniques evolve rapidly and are difficult to fully categorize. The simplest and most effective defense strategies include:
- Do not open emails from unknown senders.
- Avoid opening emails unrelated to your professional duties.
- If the sender appears familiar but the email address differs from usual, verify before opening.
- Disable email preview features in your mail client.
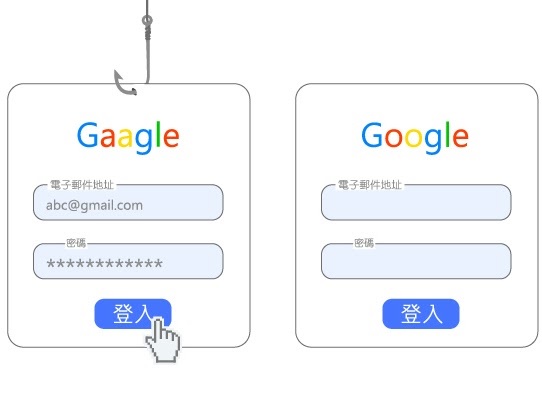
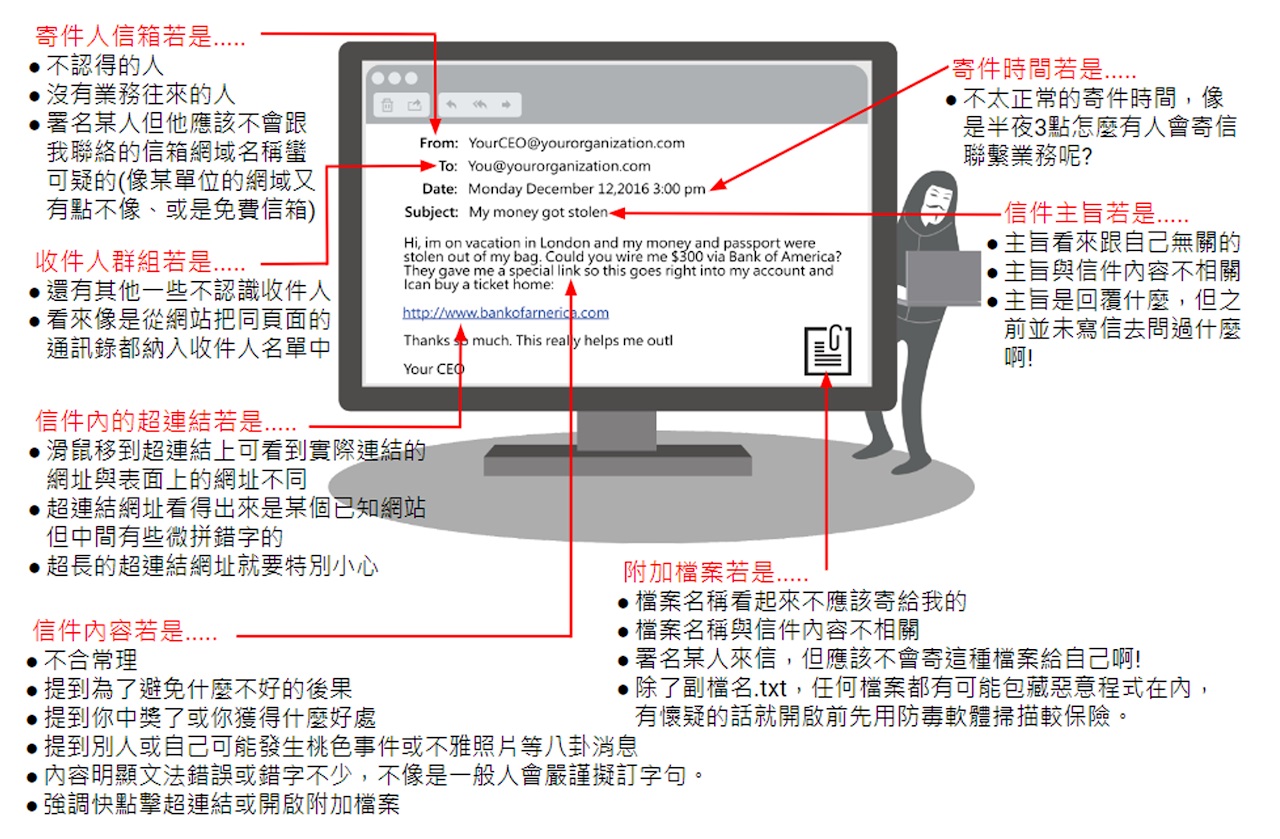
As shown in the image, attackers may impersonate well-known websites to steal your login credentials. If you are not cautious, your account may be compromised.
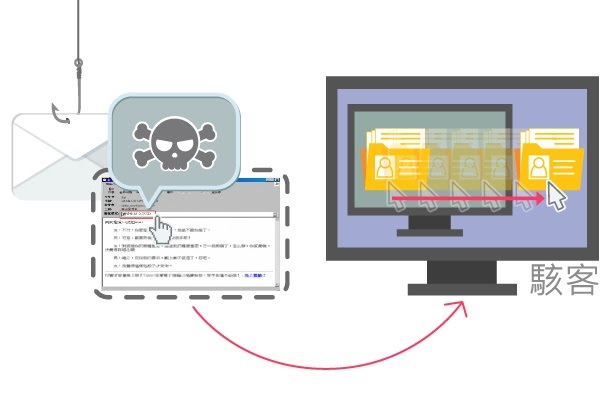
If an email attachment contains a virus, clicking on it unknowingly may result in infection by a trojan or other forms of malware. This could allow hackers to steal your personal information and access sensitive data stored on your computer.
When receiving emails, always pay close attention to the sender’s email address, time of delivery, subject line, and any attachments. If any of these elements appear suspicious, the message may be a phishing email. In such cases, do not open any attachments or click on links contained in the message.

 繁
繁  EN
EN 